What is WAF
A Web Application Firewall (WAF) is a specific type of firewall that protects web applications from threats and attacks by filtering, monitoring, and blocking potentially harmful HTTP traffic between a web application and the Internet. While traditional firewalls serve as a defense system for servers and networks, WAFs are specialized to secure web applications.
Features of WAF
-
Traffic Filtering
WAFs inspect the contents of each HTTP/HTTPS request and response to identify patterns or sequences that suggest a web attack. They utilize methods such as SQL injection detection, cross-site scripting (XSS) prevention, and HTTP protocol violation detection. -
Protection Against Specific Attacks
WAFs can defend against a variety of specific attacks, including SQL injection, XSS, and cross-site request forgery. Some WAFs also offer protection against Distributed Denial of Service (DDoS) attacks. -
HTTP Request Validation
WAFs verify the syntax of each HTTP request to ensure it complies with the protocol standards. They can detect anomalies that might indicate an attack, such as oversized headers, missing required fields, or unexpected sequences of requests. -
Session Management
WAFs can manage user sessions to protect against session hijacking and session replay attacks. By monitoring and controlling the use of session cookies, they ensure that attackers cannot impersonate legitimate users. -
Customizable Security Policies
One of the most powerful features of a WAF is the ability to create and modify security policies according to the specific needs of a web application. Administrators can configure the rules that determine which types of HTTP traffic the WAF should block, monitor, or allow. -
Reporting and Logging
WAFs provide detailed logs and reports on detected threats and attacks. This information aids in incident response, forensic analysis, and long-term security planning.
WAF vs. Firewall vs. IPS/IDS
Firewalls, WAFs, and IPS/IDS have different layers of expertise as follows.
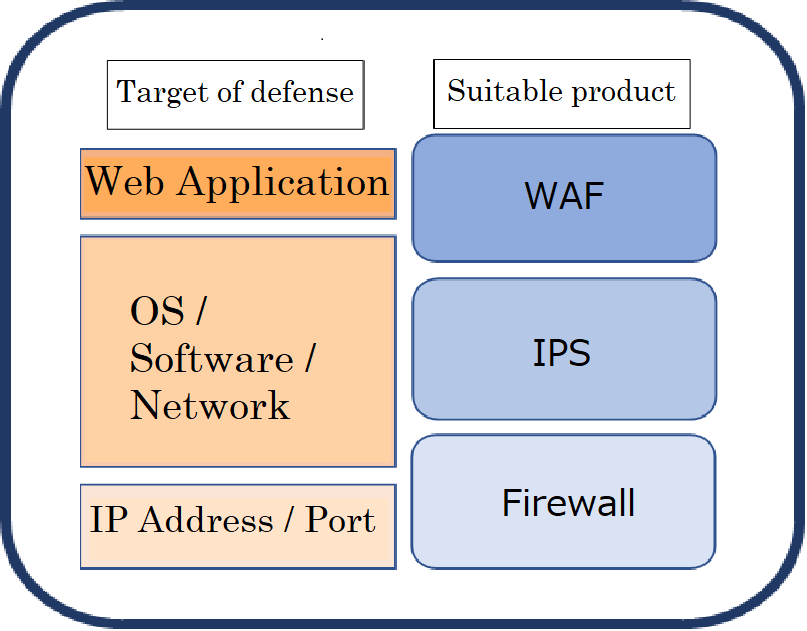
Difference between a firewall, WAF and IPS
Comparison of WAF to Traditional Firewalls
While both traditional firewalls and WAFs provide a layer of security, they operate at different levels and offer different types of protection. Traditional firewalls typically work at the network layer, monitoring all inbound and outbound traffic based on predefined security rules. In contrast, WAFs work at the application layer, monitoring, filtering, and blocking specific HTTP traffic that could harm a web application.
Pros and Cons of Each Approach
Traditional firewalls offer broad protection against a wide range of threats and are vital for securing a network as a whole. However, they are not equipped to handle more complex, application-specific threats. WAFs fill this gap by providing targeted security for web applications, although they require more in-depth, application-specific configuration.
Comparison of WAF to Intrusion Prevention Systems/Intrusion Detection Systems (IPS/IDS)
Both WAFs and IPS/IDS are designed to identify and mitigate threats. However, while IPS/IDS systems detect threats across the entire network, WAFs specifically focus on web applications. IPS/IDS systems work by identifying suspicious activities that could indicate a breach, whereas WAFs primarily prevent attacks by filtering out malicious web traffic.
How They Complement Each Other
In an optimal security setup, WAFs and IPS/IDS systems complement each other. An IPS/IDS system provides an additional layer of security by monitoring network traffic and detecting potential breaches, while a WAF adds further protection by specifically securing web applications against targeted attacks. Together, they provide a more comprehensive defense against a broader range of threats.
How WAF Works
A WAF operates through a set of rules often referred to as policies. These policies instruct the WAF on which types of traffic to block, allow, or monitor. When a request comes in, the WAF inspects it against these policies and takes appropriate action, allowing safe traffic to reach the web application and blocking potentially harmful traffic.
Signature-Based Detection
One of the primary ways that a WAF identifies threats is through signature-based detection. This method involves identifying patterns in HTTP requests that match known attack vectors. When the WAF detects a match, it blocks the suspicious request, preventing it from reaching the web application.
Blacklisting
Blacklisting is a method by which the WAF denies access based on a set of defined criteria, such as IP addresses, geographic locations, or HTTP signatures associated with known threats. Any traffic matching these criteria is automatically blocked, providing a robust defense against recognized threats.
Whitelisting
Conversely, whitelisting involves defining a list of trusted sources or behaviors. The WAF allows traffic that matches the whitelist criteria and blocks all others. This approach is generally considered more secure but can be more complex to manage, as it requires a detailed understanding of expected web application traffic.